 By John Nye, Vice President of Cybersecurity Strategy, CynergisTek
By John Nye, Vice President of Cybersecurity Strategy, CynergisTek
Twitter: @cynergistek
Twitter: @EndisNye
The US Department of Health and Human Services (HHS), Office for Civil Rights (OCR), published an advisory in the March issue of its “Cybersecurity Newsletter” warning of a well-known attack method known as the man-in-the-middle (MitM) attack. This type of attack is used by attackers to, exactly as it sounds, become a man in the middle of a secure connection. So, while the victim thinks they are connecting to their destination website (e.g. bank, social media, email, etc), the attacker is taking over the connection and can see any data “in the clear” before it is forwarded on to the actual destination.
This type of attack can be described in a very simple diagram, shown below. The top part of the image shows a normal secure connection (that has been blocked by our attacker) and the bottom shows how a MitM attack works.
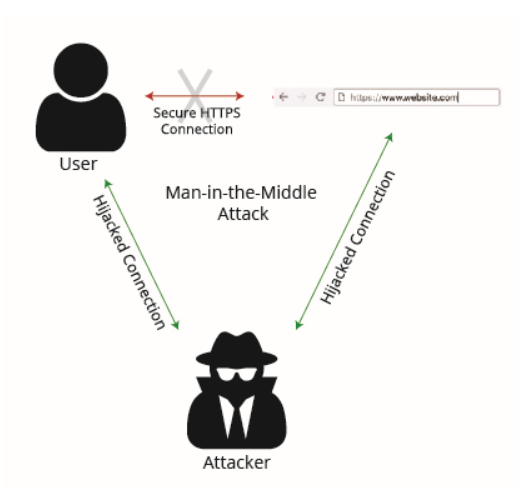
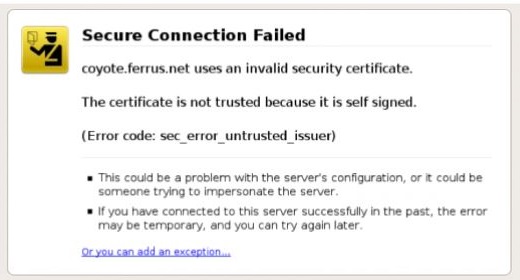
OCR went beyond warning that MitM attacks are possible. In fact, most modern devices are capable of warning users if something fishy is going on. When a user is connected directly to a legitimate secure website the browser will only show a green lock symbol (or something similar depending on the browser you are using). This is virtually seamless for the user, and there is rarely anything else to do if the website used a trusted Certificate Authority (the organizations that have been trusted across the web, like VeriSign and Google to distribute certificates). If the website is using a less-than-trusted certificate the user will see a warning something like this:
HTTPS Intercept Products
The problem is that the protections built into the browsers don’t work in large organizations that use what are commonly known as HTTPS intercept products. These devices are designed to sit between the users of an organization and the Internet. The devices’ certificates are added to the trusted store on all local systems and any traffic to an encrypted site is routed through the intercept devices. This means that regardless of the certificate on the destination website the users will see no warning because the certs on the devices are pre-approved.
The problem begins when the device talks directly to the destination website or application. Rather than the connection being established via the user’s browser, it is established directly from the intercept device. This eliminates the protections that have been put in place as the devices could accept an illegitimate certificate and the user would have no indication. This means that these devices, if they don’t verify secure connections to web hosts, make MitM attacks much simpler for attackers to perform.
Recommendations
One step that OCR recommends is to check any HTTPS Intercept devices used within the enterprise against the lists on “badssl.com” to determine if the products in use properly validates certificates. The best possible methods for remediating this issue are available in US-CERT guidance which can be found in Alert TA15-120A, the highlights of which are as follows:
- Update Transport Layer Security and Secure Socket Layer (TLS/SSL) by upgrading to TLS 1.1 or higher and making sure that all versions of SSL (1, 2, and 3) as well as TLS 1.0 are disabled.
- Use certificate pinning
- Incorporate DNS-based Authentication of Named Entities (DANE)
- Use network notary servers
OCR also recommends that covered entities and business associates using any type of HTTPS interception technology should consider the risks this could present to their ePHI. In short, these types of security products have a litany of potential pitfalls associated with them, and this potential to increase the organizations vulnerability to malicious MitM attacks should be considered carefully.
Read OCR’s monthly Cyber Awareness newsletters and other HIPAA Security Rule Guidance Material.
This article was originally published on CynergisTek and is republished here with permission.
