 What You Need to Know
What You Need to Know
By Rick Link, Managing Director, Dallas TX office of Coalfire Systems, Inc.
Twitter: @RickyRayLink
Twitter: @CoalfireITGRC
Last week the HHS Office for Civil Rights (OCR) issued their Annual Report to Congress on Breaches of Unsecured Protected Health Information (PHI) for calendar years 2011 and 2012. This is their second annual report required by the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009.
As background, all HIPAA covered entities (and now business associates) are required to notify affected individuals, the HHS Secretary, and in certain instances the media following the discovery of a breach of unsecured PHI if greater than 500 records. The Act defines “unsecured protected health information” as “protected health information that is not secured through the use of a technology or methodology specified by the Secretary in guidance” and provides that the guidance specify the processes that render the PHI unusable, unreadable, or indecipherable to unauthorized persons.
Now that you’re aware of the background, let’s explore some key data points in the most recent report for 2011 and 2012.
- The OCR received 236 reports of breaches of over 500 records during the calendar year 2011, which affected approximately 11,415,185 individuals.
- The OCR received 222 reports of breaches of over 500 records during the calendar year 2012, which affected approximately 3,273,735 individuals.
- Cumulatively, from September 23, 2009, to December 31, 2012, the OCR received 710 reports affecting approximately 22.5 million individuals.
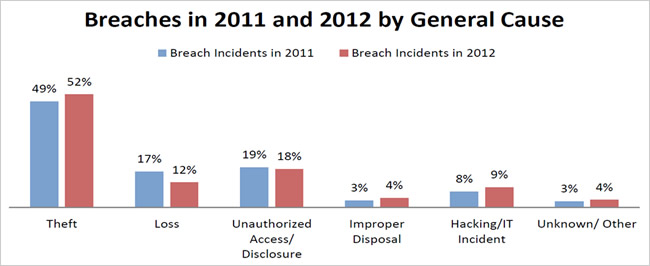
- The OCR defined the following categories for the 2011 and 2012 breaches: theft; loss; unauthorized access or disclosure; improper disposal; hacking or IT incident; and unknown or other.
The following chart shows the percentage of breaches in 2011 and 2012 categorized by six general causes of breaches.
 Remediation Action Steps Taken
Remediation Action Steps Taken
For breaches affecting 500 or more individuals that occurred in 2011 and 2012, covered entities most commonly reported taking one or more of the following steps to mitigate the potential consequences of the breaches and prevent future breaches:
- Revising policies and procedures;
- Improving physical security by installing new security systems or by relocating equipment or records to a more secure area;
- Training or retraining workforce members who handle PHI;
- Providing free credit monitoring to customers;
- Adopting encryption technologies;
- Imposing sanctions on workforce members who violated policies and procedures for removing PHI from facilities or who improperly accessed PHI, among other issues;
- Changing passwords;
- Performing a new risk assessment; and
- Revising business associate contracts to include more detailed provisions for the protection of health information.
OCR Audits of the Breach Notification Rule
The HITECH Act authorizes and requires the OCR to provide for periodic audits to ensure that covered entities and business associates comply with the HIPAA Rules. These audits provided an opportunity to examine mechanisms for compliance, identify best practices, and discover risks and vulnerabilities above the OCR’s ongoing compliance investigations and reviews. The OCR’s audit pilot program performed 115 audits of covered entities of varying types and sizes using protocol materials to assess privacy, and security compliance. All audits in the program were completed during December 2012 and focused on the specific aspects of the Breach Notification Rule:
- Notification to Individuals;
- Timeliness of Notification;
- Methods of Individual Notification; and
- Burden of Proof.
Lessons Learned
We can all learn from the breach reports in terms of areas of vulnerability in the privacy and security of individuals’ PHI. Based on the breaches reported to the OCR, below are some areas that covered entities and business associates should pay particular attention to in their compliance efforts to help avoid some of the more common types of breaches.
- Risk Analysis and Risk Management. Ensure the organization’s security risk analysis and risk management plan are thorough, having identified and addressed the potential risks and vulnerabilities to all ePHI in the environment, regardless of location or media. This includes, for example, ePHI on computer hard drives, digital copiers and other equipment with hard drives, USB drives, etc.
- Security Evaluation. Conduct a security evaluation when there are operational changes, such as facility/office moves, renovations, mergers/acquisitions, or systems upgrades, which could affect the security of PHI, and ensure that appropriate physical and technical safeguards remain in place during the changes to protect the information when stored or when in transit from one location to another.
- Security and Control of Portable Electronic Devices. Ensure that PHI, which is stored and transported on portable electronic devices, is safeguarded – including encryption where appropriate.
- Proper Disposal. Implement clear policies and procedures for the proper disposal of PHI in all forms. For electronic devices and equipment that store PHI, ensure the device or equipment is purged or wiped thoroughly before it is recycled, discarded, or transferred to a third party, such as a leasing agent.
- Physical Access Controls. Assure that physical safeguards are in place to limit access to facilities and workstations that maintain PHI.
- Training. Confirm that employees are trained on the organization’s privacy and security policies and procedures, including the appropriate uses and disclosures of PHI, and the safeguards that should be implemented to protect the information from improper uses and disclosures; and make sure that employees are aware of the sanctions and other consequences for failure to follow the organization’s policies and procedures.
With the HIPAA Omnibus Rule of 2013, many covered entities and business associates do not come close to having the basic protections required to ensure the confidentiality, integrity and availability of their PHI data. This is not new news to security professionals working in the field. Organizations should consider reviewing this HITECH report and also engaging a security and compliance firm like Coalfire, an independent IT GRC firm that will be your trusted advisor and provide a fact-based HIPAA security assessment.
About the Author: Ricky Link, Managing Director, in the Dallas, Texas office of Coalfire Systems, Inc., is a fast-growing IT Governance, Risk and Compliance firm serving as a trusted advisor to security-conscious leaders in all industry groups. He is a member of the senior management team and leads the Southwest Region offering security, audit and compliance professional services.
This article was originally published on The Coalfire Blog and is republished here with permission.
