 By Marty Puranik, Founder, President, & CEO, Atlantic.Net
By Marty Puranik, Founder, President, & CEO, Atlantic.Net
Twitter: @AtlanticNet
While the majority of HIPAA violations involve electronic data breaches, the HIPAA Security Rule requires that healthcare providers and business associates implement “physical safeguards for all workstations that access ePHI to restrict access to authorized users.”
This means that failure to comply with these rules can lead to a violation for failing to physically secure electronic devices which hold protected health information (PHI).
Of course, violations may not always be intentional, as there can be many misconceptions about HIPAA and security procedures, which is what we aim to clear up. HIPAA regulations do mostly cover electronic security measures such as firewalls, encryption, and security risk assessments, it also covers physical and administrative safeguards, which must be utilized in protecting PHI.
The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) recently introduced new information, which places emphasis on the necessity of physical security for healthcare organizations. This is partially because physical safeguards are not only effective but simple and cheap to install, leaving organizations with very little excuse for not being in compliance.
So what exactly are physical safeguards as considered by the HIPAA guidelines? Let’s explore a bit.
Physical Safeguards for HIPAA Compliance
Physical safeguards are intended to keep intruders out of workstation devices containing protected health information. HIPAA considers a workstation device to be a “computing device, for example, a laptop or desktop computer, or any other device that performs similar functions and electronic media stored in its immediate environment. This definition includes tablets, smartphones, and other portable devices”.
Some physical safeguards include things like:
- Privacy screens
- Encrypted USB drives
- Device locks
- Protected CD drives
- Two-factor authentication tokens
Aside from those types of things, HIPAA also makes recommendations for the physical location of electronic hardware. For example, electronic hardware such as servers should be kept in secured, locked areas, with minimal, role-based access. You can see the HIPAA Security Rule Checklist here.
The OCR released a security newsletter last May of 2018, which asks healthcare officials to consider the following questions when considering their approach to HIPAA physical security safeguards:
- Is there a current inventory of all electronic devices (i.e., computers, portable devices, electronic media) including where such devices are located?
- Are any devices located in public areas or areas that are vulnerable to theft, unauthorized use, or unauthorized viewing
- Should devices currently in public or vulnerable areas be relocated?
- What HIPAA physical security controls are currently in use (i.e., cable locks, privacy screens, secured rooms, cameras, guards, alarm systems) and are they easy to use?
- What additional HIPAA physical security controls can be reasonably put into place?
- Are policies in place and are employees properly trained regarding physical security (i.e., use of cable locks and privacy screens)?
- Are signs posted reminding personnel and visitors about HIPAA physical security policies or monitoring?
The newsletter even suggests physical cable locks in order to prevent theft of laptops and other hardware. While all of this sounds very simple, it is highly effective.
To illustrate their point, the OCR mentions a 2015 HIPAA settlement, involving Lahey Hospital and Medical Center, which affected 599 patients. The security breach began with the physical theft of an unencrypted laptop from the Tufts Medical School-affiliated teaching hospital.
The laptop had been stolen from an unlocked treatment room near an inner corridor of the radiology department. For this, Lahey Hospital was fined $850,000, which is no small sum for an easily avoidable situation.
Since releasing the HIPAA Security Rule’s physical safeguard standard, OCR settlement payments have ranged from $250,000 to $3.9 million for violations. Some recent examples are the Feinstein Institute for Medical Research, agreed to pay $3.9 million, and the University of Mississippi who paid $2.75 million.
How many health organizations are implementing proper security?
In the 2018 HIMSS Cybersecurity Survey, 71.1% of 239 healthcare IT respondents are including physical security in their security risk assessments. A further 81.3% of respondents have cybersecurity procedures, policies, and documentation in their risk assessment. 74.4% utilize network security, 73.5% have security awareness and training programs, while 69.3% include an inventory of assets in risk assessment.
65% of respondents said they completely replaced or upgraded their current security solutions on risk assessment results, while 83% said their organization went on to adopt better security measures. A bit more than 50% said that software, hardware, and electronic devices that were end-of-life, or deprecated, were replaced.
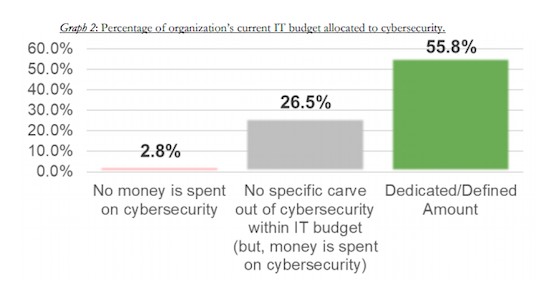
It’s been said that healthcare organizations do not set aside enough of their budget to cybersecurity. 21% said their organization reserved less than 2% of their budget to cybersecurity, while another 21% said their organization devoted only 3 to 6% of their budget.
The two biggest barriers for proper cybersecurity were a lack of financial resources, and not having the right cybersecurity personnel on their staff. This is easy to believe, as cybersecurity for healthcare organizations is, in fact, more expensive than cybersecurity for other kinds of companies. This is due to the fact that healthcare organizations use highly customized software, specific to the healthcare industry, which requires specific cybersecurity strategies.
Physical Security is Equally Important as Cybersecurity for HIPAA Compliance
The takeaway from all this is that the HHS’ Office for Civil Rights considers physical security every bit as important as cybersecurity, for good reason. Numerous health companies have found this out the hard way.
- In 2014, QCA Health Plan paid a total of $250,000 to OCR for potential HIPAA violations. QCA Health Plan had not implemented physical safeguards for their workstations, which allowed unrestricted access to ePHI data. An unencrypted laptop was stolen from an employee’s vehicle.
- Massachusetts Eye and Ear Infirmary (MEEI) was fined $1.5 million in 2012, for the same situation. An unencrypted laptop was stolen, which resulted in the exposure of ePHI data.
One thing the OCR considers when judging cases is the timeliness of reported breaches. HIPAA is clear in that breaches must be reported within 60 days after discovery. Even if an organization is still investigating the breach, the OCR does not make an exception to this rule. Healthcare attorney Corinne Smith explained it in response to questions from HealthITSecurity:
“Timing begins on when it is known, not when the investigation is complete — even if it is initially unclear whether the incident constitutes a breach as defined in the rule,” said Smith. “The 60 days is an outer limit and in some cases, it may be an unreasonable delay to wait 60 days.”
“It’s not a good idea to wait until your forensics investigation is complete before thinking about providing notice,” she continued. “It’s best to run parallel tracks – one preparing to notify patients and the other running the investigation.”
Thus, some of the largest fines have been imposed by the OCR on healthcare companies that failed to report their breaches in a timely manner.
For more resources from Atlantic.net check out these downloads:
